Participamos de um Webinar há algumas semanas atrás com o Luiz Ferreira onde batemos um papo de 1 hora sobre desafios na parte da segurança defensiva.
Assistam lá e espero que gostem!
Lembrando que em breve lançaremos nossa grade de treinamentos defensivos para esse segundo semestre com tópicos como:
- ATT&CK
- Endpoint Monitoring
- Logging & Security Analytics
- Network Security Monitoring
- Threat Hunting
Acompanhem no twitter @BlueOpsBR e em nosso site https://www.blueops.com.br
Happy Detection!
Blue Team Operations
Threat Hunter Brasil
Grupo de Caçadores de Ameaças, com foco em divulgação de conhecimento com situações do dia a dia, treinamentos (EaD e in loco) e consultorias.
sexta-feira, 20 de julho de 2018
sexta-feira, 6 de julho de 2018
Measuring Operational Risks using Mitre {ATT&CK,Navigator} and Elastic Stack
First of all, we know that we should write in Portuguese, but this blogpost deserves to fly abroad Terra Brasilis, so we are opening an exception.
ATT&CK Introduction (retrieved from mitre attack website)
With data ingested in our Elasticsearch we created some views:
To download Kibana stuff https://github.com/spookerlabs/kibana_attack
Some ideas we have in mind for the future:
ATT&CK Introduction (retrieved from mitre attack website)
"Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) for Enterprise is an adversary model and framework for describing the actions an adversary may take to compromise and operate within an enterprise network. The model can be used to better characterize and describe post-compromise adversary behavior. It both expands the knowledge of network defenders and assists in prioritizing network defense by detailing the tactics, techniques, and procedures (TTPs) cyber threats use to gain access and execute their objectives while operating inside a network.
ATT&CK for Enterprise incorporates information on cyber adversaries gathered through MITRE research, as well as from other disciplines such as penetration testing and red teaming to establish a collection of knowledge characterizing the activities adversaries use against enterprise networks. While there is significant research on initial exploitation and use of perimeter defenses, there is a gap in central knowledge of adversary process after initial access has been gained. ATT&CK for Enterprise focuses on TTPs adversaries use to make decisions, expand access, and execute their objectives. It aims to describe an adversary's steps at a high enough level to be applied widely across platforms, but still maintain enough details to be technically useful.
The 11 tactic categories within ATT&CK for Enterprise were derived from the later stages (exploit, control, maintain, and execute) of a seven-stage Cyber Attack Lifecycle[1] (first articulated by Lockheed Martin as the Cyber Kill Chain®[2]). This provides a deeper level of granularity in describing what can occur during an intrusion.
Each category contains a list of techniques that an adversary could use to perform that tactic. Techniques are broken down to provide a technical description, indicators, useful defensive sensor data, detection analytics, and potential mitigations. Applying intrusion data to the model then helps focus defense on the commonly used techniques across groups of activity and helps identify gaps in security. Defenders and decision makers can use the information in ATT&CK for Enterprise for various purposes, not just as a checklist of specific adversarial techniques.
ATT&CK for Enterprise incorporates details from multiple operating system platforms commonly found within enterprise networks, including Microsoft Windows, macOS, and Linux. The framework and higher level categories may also be applied to other platforms and environments. To view the contents of ATT&CK for Enterprise, use the left navigation pane, which breaks out techniques by tactic category or view All Techniques."
Based on ATT&CK we can take a snapshot of our company security state on each tactic and technique, knowing where we have better detection and where we should invest more efforts. So in our mind and talking about this during a ATT&CK training we were teaching, the question was how to create a visualization for this and decide quickly how to prioritize an IDS alert, or a vulnerability found or new technology we need to deploy to cover gaps ? The answer that we found was using Navigator Scoring with Elastic Stack.
ATT&CK for Enterprise incorporates information on cyber adversaries gathered through MITRE research, as well as from other disciplines such as penetration testing and red teaming to establish a collection of knowledge characterizing the activities adversaries use against enterprise networks. While there is significant research on initial exploitation and use of perimeter defenses, there is a gap in central knowledge of adversary process after initial access has been gained. ATT&CK for Enterprise focuses on TTPs adversaries use to make decisions, expand access, and execute their objectives. It aims to describe an adversary's steps at a high enough level to be applied widely across platforms, but still maintain enough details to be technically useful.
The 11 tactic categories within ATT&CK for Enterprise were derived from the later stages (exploit, control, maintain, and execute) of a seven-stage Cyber Attack Lifecycle[1] (first articulated by Lockheed Martin as the Cyber Kill Chain®[2]). This provides a deeper level of granularity in describing what can occur during an intrusion.
Each category contains a list of techniques that an adversary could use to perform that tactic. Techniques are broken down to provide a technical description, indicators, useful defensive sensor data, detection analytics, and potential mitigations. Applying intrusion data to the model then helps focus defense on the commonly used techniques across groups of activity and helps identify gaps in security. Defenders and decision makers can use the information in ATT&CK for Enterprise for various purposes, not just as a checklist of specific adversarial techniques.
ATT&CK for Enterprise incorporates details from multiple operating system platforms commonly found within enterprise networks, including Microsoft Windows, macOS, and Linux. The framework and higher level categories may also be applied to other platforms and environments. To view the contents of ATT&CK for Enterprise, use the left navigation pane, which breaks out techniques by tactic category or view All Techniques."
Based on ATT&CK we can take a snapshot of our company security state on each tactic and technique, knowing where we have better detection and where we should invest more efforts. So in our mind and talking about this during a ATT&CK training we were teaching, the question was how to create a visualization for this and decide quickly how to prioritize an IDS alert, or a vulnerability found or new technology we need to deploy to cover gaps ? The answer that we found was using Navigator Scoring with Elastic Stack.
So how we could do that with them?
Basically Mitre Navigator you can fill techniques with some Score based on tools you have or initially just based on "feelings". After you filled all the techniques you will have something like this:
We really suggest you split into minor areas, network segmentation, department this but in a very first step have a general one is a good start.
So having this read you have how to add Layer Name and Description (In our sample we configure Layer as "Company" and Description as "Network Segment")
After filling your matrix, you can download it as a JSON file. The only problem with JSON I found it was that logstash JSON filter can't parse it directly you I just remove newlines with some basic bash.
Regular JSON download
File ready, time to parse and send it to Elasticsearch. We just created a basic config to create this PoC that we have ideas to enrich with more information in a second part.
Config:
input {stdin {}}
filter {
json { source => message }
split {
field => "techniques"
}
mutate { remove_field => [ "gradient", "filters", "hideDisabled", "tacticRowBackground", "legendItems", "sorting","showTacticRowBackground", "viewMode", "selectTechniquesAcrossTactics","version" , "@version" , "[techniques][color]", "[techniques][enabled]", "message"] }
}
output {elasticsearch { index => navigator }}
Debug Output:
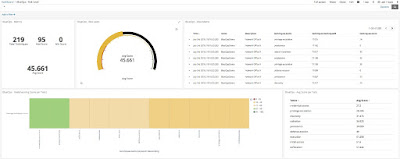
With data ingested in our Elasticsearch we created some views:
To download Kibana stuff https://github.com/spookerlabs/kibana_attack
Some ideas we have in mind for the future:
- Create a database about defense tools mapped with ATT&CK and correlate your status and needs
- Tool to quickly correlate a Pentest/VA report and prioritize vulnerability affects more your network
- Compare you security risk with groups or something you read and map.
- Integrate / Compatibility with HELK project
- Enrich information using translate at logstash
- Auto update scoring using Red Team automation / tests
- Add ATT&CK Pre
If you have something in mind let us know. Hope it helps!
Happy Detection!
Blue Team Operations
- Enrich information using translate at logstash
- Auto update scoring using Red Team automation / tests
- Add ATT&CK Pre
If you have something in mind let us know. Hope it helps!
Happy Detection!
Blue Team Operations
quarta-feira, 20 de junho de 2018
Fazendo tracking do login usuário e comandos no seu endpoint Linux com Audit e Elastic Stack
Já vimos no post anterior uma visão básica do Audit e seu potencial. Uma pergunta que sempre escuto é como monitorar todos comandos que são utilizados pelos usuários que acessam servidores ou até mesmo dos desktops com linux. Pensando nisso fizemos um laboratório rápido para ilustrar como é possível criar essa auditora rapidamente utilizando como base o CentOS.
Por padrão o audit linux já vem habilitado no CentOS, porém sem regras adicionadas. O primeiro ponto então é que regras devemos utilizar para ter esse controle. Sem pensar muito (logicamente com muito mais que precisamos pra isso , porém mais visibilidade ainda) indico o trabalho do Florian Roth que concatenou várias regras e sugestões num gist público
Link: https://gist.github.com/Neo23x0/9fe88c0c5979e017a389b90fd19ddfee
Em resumo você precisa copiar esse conteúdo para o /etc/audit/conf.d/audit.rules e reinicar o serviço do auditd. Lembre-se de confirmar que as regras entraram em ação com o auditctl -l.
Com isso criado, basicamente configurei meu logstash para parsear as informações, deixando ela BEM granulizada pois assim conseguimos filtrar e criar visualizações para tudo que necessitarmos. Os eventos do audit possuem dezenas de campos e para minha felicidade postaram um guia com todos os campos e explicações de cada que vocês podem aprender e entender melhor acessando :
Link: https://github.com/bfuzzy/Linux-Audit-Events/blob/master/Linux_Audit_Event_Fields.md
Após o entendimento e evento sendo salvos na stack elastic, o que precisamos ter em mente é o que queremos. No meu exemplo quero saber:
- Usuário origem
- IP Origem
- Comandos digitados
Com essa pergunta em mente, basicamente o que preciso é pegar o tipo USER_LOGIN, da onde se é gerado um campo chamado ses que é carregado para o tipo SYSCALL e consequentemente analisarei o tipo PROCTITLE que terá o comando digitado.
A tela inicial de evento salvos podem ser visto aqui:
Após isso, para adiantar minhas análises criei algumas visualizações que mostrarei na sequência para um drilldown
Nessa visualização pegaremos o audit_ses (436) e usaremos de filtro
Para facilitar o processo, criamos um script onde eu colocando a sessão eu mapeio todos os comandos da sessão de forma rápida e via linha de comando.
Além de uso para monitorar usuários, um ponto legal também é para Honeypots de alta interatividade.
Agora para ficar melhor a visualização, temos o vídeo com todo processo
No próximo post, compartilharemos a config do Logstash bem como o script em python para maior rapidez na resposta a análises necessárias.
Aproveitando, se quiser aprender mais sobre logging com elastic, entender eventos entre outros assuntos importantes no lado defensivo não deixe de fazer nosso treinamento https://blueops.com.br/treinamento/gerencia-logs/
Happy Detection!
Equipe Blue Ops
Por padrão o audit linux já vem habilitado no CentOS, porém sem regras adicionadas. O primeiro ponto então é que regras devemos utilizar para ter esse controle. Sem pensar muito (logicamente com muito mais que precisamos pra isso , porém mais visibilidade ainda) indico o trabalho do Florian Roth que concatenou várias regras e sugestões num gist público
Link: https://gist.github.com/Neo23x0/9fe88c0c5979e017a389b90fd19ddfee
Em resumo você precisa copiar esse conteúdo para o /etc/audit/conf.d/audit.rules e reinicar o serviço do auditd. Lembre-se de confirmar que as regras entraram em ação com o auditctl -l.
Com isso criado, basicamente configurei meu logstash para parsear as informações, deixando ela BEM granulizada pois assim conseguimos filtrar e criar visualizações para tudo que necessitarmos. Os eventos do audit possuem dezenas de campos e para minha felicidade postaram um guia com todos os campos e explicações de cada que vocês podem aprender e entender melhor acessando :
Link: https://github.com/bfuzzy/Linux-Audit-Events/blob/master/Linux_Audit_Event_Fields.md
Após o entendimento e evento sendo salvos na stack elastic, o que precisamos ter em mente é o que queremos. No meu exemplo quero saber:
- Usuário origem
- IP Origem
- Comandos digitados
Com essa pergunta em mente, basicamente o que preciso é pegar o tipo USER_LOGIN, da onde se é gerado um campo chamado ses que é carregado para o tipo SYSCALL e consequentemente analisarei o tipo PROCTITLE que terá o comando digitado.
A tela inicial de evento salvos podem ser visto aqui:
Após isso, para adiantar minhas análises criei algumas visualizações que mostrarei na sequência para um drilldown
Nessa visualização pegaremos o audit_ses (436) e usaremos de filtro
Para facilitar o processo, criamos um script onde eu colocando a sessão eu mapeio todos os comandos da sessão de forma rápida e via linha de comando.
Além de uso para monitorar usuários, um ponto legal também é para Honeypots de alta interatividade.
Agora para ficar melhor a visualização, temos o vídeo com todo processo
No próximo post, compartilharemos a config do Logstash bem como o script em python para maior rapidez na resposta a análises necessárias.
Aproveitando, se quiser aprender mais sobre logging com elastic, entender eventos entre outros assuntos importantes no lado defensivo não deixe de fazer nosso treinamento https://blueops.com.br/treinamento/gerencia-logs/
Happy Detection!
Equipe Blue Ops
quarta-feira, 6 de junho de 2018
Introdução ao monitoramento de endpoint Linux com o audit
Um dos pontos críticos que temos na área defensiva é justamente saber o que acontece na máquina, seja de forma regular ou maliciosa, mas alguma forma de fazer o tracking da origem conexão, usuário, ações executadas entre outros pontos. Existe em praticamente todo Sistema Operacional algum sistema de auditoria escutando por isso, muitas vezes apenas esperando ser habilitado ou configurado.
No caso do Linux temos o Audit, que por padrão no CentOS vem instalado e habilitado, porém sem regras. O Audit do linux podemos monitorar tudo que acontece no sistema baseado nas 330+ syscall existentes.
A arquitetura do audit basicamente é representada nessa imagem:
Você tem aplicações, processos, comandos sendo executados no userland e "comunicando com o kernel", sendo que o audit pega essas infos diretamente lá e joga de volta para o sistema no userland.
A estrutura do audit instalado no SO é a seguinte:
Configurações => /etc/audit/
Regras => /etc/audit/rules.d/
Eventos => /var/log/audit/
Existe alguns comandos para ver quais as configurações existente, pesquisar eventos gerados e relatórios
auditctl
ausearch
aureport
Para simularmos algo simples, criarei uma regra para monitorar arquivos binários que por simulação considero suspeito que seriam whoami e tcpdump
Inicialmente sem regras:
Repetindo os comandos acima (não colando novamente para não alongar o post)
O audit é extremamente poderoso e possui uma granularidade muito interessante nas informações que geram. Em próximas postagens falaremos mais específico sobre regras e campos, integração com Stack Elastic, osquery e alguns casos de monitoramento.
Link excelente documentação da Redhat: https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security_guide/chap-system_auditing
Happy Hunting!
Equipe BlueOps
No caso do Linux temos o Audit, que por padrão no CentOS vem instalado e habilitado, porém sem regras. O Audit do linux podemos monitorar tudo que acontece no sistema baseado nas 330+ syscall existentes.
A arquitetura do audit basicamente é representada nessa imagem:
Você tem aplicações, processos, comandos sendo executados no userland e "comunicando com o kernel", sendo que o audit pega essas infos diretamente lá e joga de volta para o sistema no userland.
A estrutura do audit instalado no SO é a seguinte:
Configurações => /etc/audit/
Regras => /etc/audit/rules.d/
Eventos => /var/log/audit/
Existe alguns comandos para ver quais as configurações existente, pesquisar eventos gerados e relatórios
auditctl
ausearch
aureport
Para simularmos algo simples, criarei uma regra para monitorar arquivos binários que por simulação considero suspeito que seriam whoami e tcpdump
Inicialmente sem regras:
[root@BlueOpsLabs rules.d]# ausearch -i -k blueopsdemo
<no matches>
[root@BlueOpsLabs rules.d]# tcpdump -c1
<REMOVED>
1 packet captured
7 packets received by filter
0 packets dropped by kernel
[root@BlueOpsLabs rules.d]# whoami
root
[root@BlueOpsLabs rules.d]# ausearch -i -k blueopsdemo
<no matches>
[root@BlueOpsLabs rules.d]#
Após os testes, podemos ver que nada foi gerado. Para gerar, precisamos de regras e aqui criei 2regras básicas monitorando o caminho binário -w e quando a permissão execução entrar em ação -x p e salvando com a key blueopsdemo
[root@BlueOpsLabs rules.d]# cat blueops.rules
-w /usr/sbin/tcpdump -p x -k blueopsdemo
-w /usr/bin/whoami -p x -k blueopsdemo
[root@BlueOpsLabs rules.d]#
Restart e regras adicionadas
[root@BlueOpsLabs rules.d]# service auditd restart
Stopping logging: [ OK ]
Redirecting start to /bin/systemctl start auditd.service
[root@BlueOpsLabs rules.d]# ausearch -i -k blueopsdemo
----
type=CONFIG_CHANGE msg=audit(06-06-2018 15:12:41.294:55348) :
auid=unset ses=unset subj=system_u:system_r:unconfined_service_t:s0
op=add_rule key=blueopsdemo list=exit res=yes
----
type=CONFIG_CHANGE msg=audit(06-06-2018 15:12:41.295:55350) :
auid=unset ses=unset subj=system_u:system_r:unconfined_service_t:s0
op=add_rule key=blueopsdemo list=exit res=yes
[root@BlueOpsLabs rules.d]#
Repetindo os comandos acima (não colando novamente para não alongar o post)
----
type=PROCTITLE msg=audit(06-06-2018 15:14:22.393:55352) :
proctitle=tcpdump -c1
type=PATH msg=audit(06-06-2018 15:14:22.393:55352) :
item=1 name=/lib64/ld-linux-x86-64.so.2 inode=87703 dev=fd:01 mode=file,755
ouid=root ogid=root rdev=00:00 obj=system_u:object_r:ld_so_t:s0
objtype=NORMAL cap_fp=none cap_fi=none cap_fe=0 cap_fver=0
type=PATH msg=audit(06-06-2018 15:14:22.393:55352) :
item=0 name=/usr/sbin/tcpdump inode=543204 dev=fd:01 mode=file,755
ouid=root ogid=root rdev=00:00 obj=system_u:object_r:netutils_exec_t:s0
objtype=NORMAL cap_fp=none cap_fi=none cap_fe=0 cap_fver=0
type=CWD msg=audit(06-06-2018 15:14:22.393:55352) :
cwd=/etc/audit/rules.d
type=EXECVE msg=audit(06-06-2018 15:14:22.393:55352) :
argc=2 a0=tcpdump a1=-c1
type=SYSCALL msg=audit(06-06-2018 15:14:22.393:55352) :
arch=x86_64 syscall=execve success=yes exit=0 a0=0x19ea8e0
a1=0x19eae90 a2=0x19bde70 a3=0x7ffdd8102e60 items=2 ppid=887
pid=5481 auid=root uid=root gid=root euid=root suid=root
fsuid=root egid=root sgid=root fsgid=root tty=pts1 ses=105
comm=tcpdump exe=/usr/sbin/tcpdump
subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 key=blueopsdemo
----
type=PROCTITLE msg=audit(06-06-2018 15:14:30.373:55355) :
proctitle=whoami
type=PATH msg=audit(06-06-2018 15:14:30.373:55355) :
item=1 name=/lib64/ld-linux-x86-64.so.2 inode=87703 dev=fd:01
mode=file,755 ouid=root ogid=root rdev=00:00
obj=system_u:object_r:ld_so_t:s0 objtype=NORMAL
cap_fp=none cap_fi=none cap_fe=0 cap_fver=0
type=PATH msg=audit(06-06-2018 15:14:30.373:55355) :
item=0 name=/usr/bin/whoami inode=12611372 dev=fd:01
mode=file,755 ouid=root ogid=root rdev=00:00
obj=system_u:object_r:bin_t:s0 objtype=NORMAL
cap_fp=none cap_fi=none cap_fe=0 cap_fver=0
type=CWD msg=audit(06-06-2018 15:14:30.373:55355) :
cwd=/etc/audit/rules.d
type=EXECVE msg=audit(06-06-2018 15:14:30.373:55355) :
argc=1 a0=whoami
type=SYSCALL msg=audit(06-06-2018 15:14:30.373:55355) :
arch=x86_64 syscall=execve success=yes exit=0
a0=0x19eaab0 a1=0x19e0540 a2=0x19bde70
a3=0x7ffdd8102e60 items=2 ppid=887 pid=5482
auid=root uid=root gid=root euid=root suid=root fsuid=root
egid=root sgid=root fsgid=root tty=pts1 ses=105
comm=whoami exe=/usr/bin/whoami
subj=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
key=blueopsdemo
----
Link excelente documentação da Redhat: https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/security_guide/chap-system_auditing
Happy Hunting!
Equipe BlueOps
segunda-feira, 14 de maio de 2018
Analyzing apps table with osquery - Something weird with GotoMeeting
We were doing some test and queries using Facebook osquery to create some packs and noticed something not common when analyzing apps table.
osquery> SELECT name, bundle_short_version, bundle_version, bundle_identifier FROM apps WHERE name LIKE '%gotomeeting%';
+------------------------+----------------------+----------------+-------------------------+
| name | bundle_short_version | bundle_version | bundle_identifier |
+------------------------+----------------------+----------------+-------------------------+
| GoToMeeting.app | 8.24.0.8569 | 8569 | com.logmein.GoToMeeting |
| GoToMeeting (8404).app | 8.21.0.8404 | 8404 | com.logmein.GoToMeeting |
| GoToMeeting (8473).app | 8.22.0.8473 | 8473 | com.logmein.GoToMeeting |
| GoToMeeting (8557).app | 8.23.0.8557 | 8557 | com.logmein.GoToMeeting |
| GoToMeeting (8569).app | 8.24.0.8569 | 8569 | com.logmein.GoToMeeting |
| GoToMeeting (8625).app | 8.25.0.8625 | 8625 | com.logmein.GoToMeeting |
| GoToMeeting (8679).app | 8.26.0.8679 | 8679 | com.logmein.GoToMeeting |
| GoToMeeting (8789).app | 8.27.0.8789 | 8789 | com.logmein.GoToMeeting |
+------------------------+----------------------+----------------+-------------------------+
osquery>
As you can see, multiples version of GotoMeeting were found. Analyzing a bit we noticed that main GotoMeeting application was pointing to an old version (in red) and not current one (in green).
osquery> SELECT name, bundle_short_version, bundle_version, bundle_identifier FROM apps WHERE name LIKE '%gotomeeting%';
+------------------------+----------------------+----------------+-------------------------+
| name | bundle_short_version | bundle_version | bundle_identifier |
+------------------------+----------------------+----------------+-------------------------+
| GoToMeeting.app | 8.24.0.8569 | 8569 | com.logmein.GoToMeeting |
| GoToMeeting (8404).app | 8.21.0.8404 | 8404 | com.logmein.GoToMeeting |
| GoToMeeting (8473).app | 8.22.0.8473 | 8473 | com.logmein.GoToMeeting |
| GoToMeeting (8557).app | 8.23.0.8557 | 8557 | com.logmein.GoToMeeting |
| GoToMeeting (8569).app | 8.24.0.8569 | 8569 | com.logmein.GoToMeeting |
| GoToMeeting (8625).app | 8.25.0.8625 | 8625 | com.logmein.GoToMeeting |
| GoToMeeting (8679).app | 8.26.0.8679 | 8679 | com.logmein.GoToMeeting |
| GoToMeeting (8789).app | 8.27.0.8789 | 8789 | com.logmein.GoToMeeting |
+------------------------+----------------------+----------------+-------------------------+
osquery>
If you look into Mac Applications we have:
Clicking to open GotoMeeting it'll open version 8.24.
Some questions:
- Is something wrong in my Mac or it's a real problem ? (hope so , because if it isn't, this is a huge attack surface)
- Why main Application is not pointing to correct version ?
- Why they keep all old binaries version ?
Could someone test and validate more ? I didn't have another Mac to validate this or with GotoMeeting installed since very long time ago.
Happy Hunting.
BlueOps Team
Marcadores:
blueteam,
osquery,
security,
threat hunting
segunda-feira, 20 de novembro de 2017
Aumentando visibilidade nos endpoints com Facebook OSQUERY
Nas últimas semanas fizemos 3 apresentações introdutórias sobre OSQuery, Kolide Fleet e Elastic Stack, sendo Roadsec PRO SP, Roadsec Encerramento SP e na BHack em Belo Horizonte com o título "Threat Hunting e Visibilidade em endpoint com o Facebook OSQUERY".
A ideia dessa palestra foi mostrar o poder e a visibilidade de endpoint que a ferramenta OSQuery proporciona, aproveitando também para dar uma rápida introdução a ferramentas auxiliares que ajudam no gerenciamento e alertas para melhor automação.
"Você responderia rapidamente quais versões de software suas estações / servidores estão utilizando? E quais portas estão em escuta? Ou Últimos usuários ou softwares recentemente adicionados a máquina? Pensando neste ponto cego existente na grande maioria das organizações, vamos apresentar o projeto OSQuery criado pelo facebook, e sua integração com a Elastic Stack, aumentando assim a visibilidade dos seus dispositivos, ajudando assim seus analistas terem respostas quase imediatas sobre qualquer pergunta relacionada aos dispositivos bem como dashboards e alertas para um monitoramento proativo."
Para resumir, o OSQuery permite realizar consultas(queries) no seu sistema operacional e de tudo que tem nele (softwares, registros, configurações, patches, portas em escuta, processos rodando entre diversas outras coisas). Os resultados aparecem divididos em tabelas tal qual ocorre nos bancos de dados SQL. A enorme gama de consultas e as combinações de queries com join, sort, etc... permitem obter informações detalhadas de cada endpoint, quase que instantaneamente. O que é perfeito para threat hunting em endpoints.
O OSQuery é, como quase tudo que utilizamos, um software opensource, criado e mantido por engenheiros do Facebook. Um dos pontos interessantes é que ele é multiplataforma com suporte para Windows, Mac, Linux e FreeBSD.
Com intuito de um compartilhamento inicial sobre o assunto, abaixo estão os slides e demos que utilizamos, onde cobrimos tópicos como:
- osqueryi
- queries
- distributed queries
- discovery queries
- schedule / packs
- FIM (file integrity monitoring)
- Process Events
- kolide fleet
- elastic stack
Segue as duas demos com na narração meio gripada =)
osqueryi
Kolide Fleet
Pretendemos fazer posts mais específicos com os assuntos, bem como queries interessantes, monitoramentos de ameaças de momento, dicas e resolução de problemas. Adicionaremos o osquery também nos cursos de defesa do BlueOps pois o conteúdo oferecido pela ferramenta agrega valores em diversas grades dos treinamentos.
Happy Detection!
Blue Team Operations (BlueOps)
Marcadores:
blueteam,
endpoint,
osquery,
security,
siem,
threathunting,
threatintel
segunda-feira, 28 de agosto de 2017
SRW ( Snort Rules Week ) - Edição 1
Muito tempo atrás em meu blog pessoal eu postava updates que o projeto EmergingThreat e VRT (Sourcefire) fizeram em suas regras, com alguns comentários e dicas, alguns casos até com payloads caso fosse possível. Como estamos reestruturando a idéia, honeypots e laboratórios, nessa primeira edição basicamente postaremos uma visão geral dos updates baseado no sid_changes.log do pulledpork em um Sensor que será demo e atualizado hoje..
Explicando o que é o PulledPork, em resumo é uma ferramenta de atualização e gerenciamento de regras para Suricata / Snort IDS. Seu código pode ser analisado e estudado em https://github.com/shirkdog/pulledpork.
New Rules
APP-DETECT HTTPTunnel proxy outbound connection detected (1:43565)
BROWSER-FIREFOX Mozilla Firefox Javascript contentWindow in an iframe exploit attempt (1:43706)
BROWSER-FIREFOX Mozilla Firefox design mode deleted style memory corruption attempt (1:43643)
BROWSER-FIREFOX Mozilla Firefox display moz-deck style memory corruption attempt (1:43644)
BROWSER-FIREFOX Mozilla Firefox large window null pointer dereference attempt (1:43651)
BROWSER-FIREFOX Mozilla Firefox large window null pointer dereference attempt (1:43652)
BROWSER-FIREFOX Mozilla Firefox multiple vulnerabilities memory corruption attempt (1:43642)
BROWSER-FIREFOX Mozilla products obfuscated cross site scripting attempt (1:43672)
BROWSER-FIREFOX Mozilla products obfuscated cross site scripting attempt (1:43673)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43656)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43657)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43658)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43659)
BROWSER-IE Microsoft Internet Explorer 11 CMarkup GetMarkupTitle use-after-free attempt (1:43664)
BROWSER-IE Microsoft Internet Explorer 11 CMarkup GetMarkupTitle use-after-free attempt (1:43665)
BROWSER-IE Microsoft Internet Explorer CDocument use after free attempt (1:43648)
BROWSER-IE Microsoft Internet Explorer EUC-JP encoding cross site scripting attempt (1:43635)
BROWSER-IE Microsoft Internet Explorer EUC-JP encoding cross site scripting attempt (1:43636)
BROWSER-IE Microsoft Internet Explorer GDI VML gradient size heap overflow attempt (1:43622)
BROWSER-IE Microsoft Internet Explorer object type confusion remote code execution attempt (1:43598)
BROWSER-IE Microsoft Internet Explorer object type confusion remote code execution attempt (1:43599)
BROWSER-IE Microsoft Internet Explorer span tag memory corruption attempt (1:43550)
BROWSER-IE Microsoft Internet Explorer span tag memory corruption attempt (1:43551)
BROWSER-IE Microsoft Internet Explorer type confusion attempt (1:43579)
BROWSER-IE Microsoft Internet Explorer type confusion attempt (1:43580)
BROWSER-PLUGINS HP Photo Creative ActiveX clsid access attempt (1:43607)
BROWSER-PLUGINS IBM SPSS Statistics ActiveX clsid access attempt (1:43537)
BROWSER-PLUGINS IBM SPSS Statistics ActiveX clsid access attempt (1:43538)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43701)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43702)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43703)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43704)
BROWSER-PLUGINS Microsoft Access Snapshot Viewer ActiveX function call access attempt (1:43605)
BROWSER-PLUGINS Microsoft Access Snapshot Viewer ActiveX function call access attempt (1:43606)
BROWSER-PLUGINS Ultra Crypto Component ActiveX clsid access attempt (1:43649)
BROWSER-PLUGINS Ultra Crypto Component ActiveX clsid access attempt (1:43650)
ET CNC Ransomware Tracker Reported CnC Server TCP group 159 (1:2404716)
ET CNC Ransomware Tracker Reported CnC Server UDP group 159 (1:2404717)
ET CNC Shadowserver Reported CnC Server Port 33333 Group 1 (1:2405067)
ET CNC Shadowserver Reported CnC Server Port 40669 Group 1 (1:2405068)
ET CNC Shadowserver Reported CnC Server TCP group 49 (1:2404096)
ET CNC Shadowserver Reported CnC Server UDP group 49 (1:2404097)
ET CURRENT_EVENTS Disdain EK Flash Exploit M1 Aug 23 2017 (1:2024609)
ET CURRENT_EVENTS Disdain EK Flash Exploit M2 Aug 23 2017 (1:2024610)
ET CURRENT_EVENTS Disdain EK Flash Exploit M3 Aug 23 2017 (1:2024611)
ET CURRENT_EVENTS Disdain EK Landing Aug 23 2017 (1:2024612)
ET CURRENT_EVENTS Disdain EK Payload Aug 23 2017 (1:2024608)
ET CURRENT_EVENTS Disdain EK URI Struct Aug 23 2017 M1 (1:2024606)
ET CURRENT_EVENTS Disdain EK URI Struct Aug 23 2017 M2 (1:2024607)
ET CURRENT_EVENTS Hancitor/Tordal Document Inbound (1:2024605)
ET CURRENT_EVENTS Hancitor/Tordal Document Request (1:2024604)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP AX (1:2024553)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP AX M2 (1:2024602)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M1 (1:2024550)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M2 (1:2024551)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M3 (1:2024552)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt (1:2024537)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B641 (1:2024534)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B642 (1:2024535)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B643 (1:2024536)
ET CURRENT_EVENTS Possible Maldoc Downloader Aug 18 2017 (1:2024600)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Aug 19 2016 (1:2024560)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 07 2016 (1:2024568)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 13 2016 (1:2024569)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 20 2016 (1:2024570)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 27 2016 (1:2024571)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024554)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024555)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024556)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 03 2017 (1:2024572)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 12 2017 (1:2024573)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 17 2017 (1:2024574)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 17 2017 (1:2024575)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 06 2017 (1:2024580)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 10 2017 (1:2024581)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 11 2017 (1:2024582)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 13 (1:2024558)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jun 08 2017 (1:2024579)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jun 8 (1:2024557)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 24 2017 (1:2024576)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 25 2017 (1:2024577)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 31 2017 (1:2024578)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 15 2016 (1:2024565)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 16 2016 (1:2024566)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 22 2016 (1:2024567)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 13 (1:2024562)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 25 (1:2024563)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 26 (1:2024564)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Sept 2 (1:2024561)
ET CURRENT_EVENTS Possible Successful Phish - Verify Email Error Message M1 Aug 14 2017 (1:2024541)
ET CURRENT_EVENTS Possible Successful Phish - Verify Email Error Message M2 Aug 14 2017 (1:2024542)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B641 (1:2024538)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B642 (1:2024539)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B643 (1:2024540)
ET CURRENT_EVENTS Possible YapiKredi Bank (TR) Phish - Landing Page - Title over non SSL (1:2024583)
ET CURRENT_EVENTS Successful Adobe Online Phish Aug 16 2016 (1:2024559)
ET CURRENT_EVENTS Successful Interac Phish Aug 18 2017 (1:2024599)
ET CURRENT_EVENTS Successful Mail.ru Phish Aug 10 2017 (1:2024532)
ET CURRENT_EVENTS Successful Paypal Phish M1 Aug 14 2017 (1:2024544)
ET CURRENT_EVENTS Successful Paypal Phish M2 Aug 14 2017 (1:2024545)
ET CURRENT_EVENTS Successful Paypal Phish M3 Aug 14 2017 (1:2024546)
ET CURRENT_EVENTS Successful RBC Royal Bank Phish M1 Aug 17 2017 (1:2024586)
ET CURRENT_EVENTS Successful RBC Royal Bank Phish M2 Aug 17 2017 (1:2024587)
ET CURRENT_EVENTS Successful Square Phish Nov 16 2015 (1:2024547)
ET CURRENT_EVENTS Windows Scriptlet Invoking Powershell Likely Malicious (1:2024549)
ET DOS CLDAP Amplification Reflection (PoC based) (1:2024584)
ET DOS Potential CLDAP Amplification Reflection (1:2024585)
ET EXPLOIT Ubiquiti Networks UniFi Cloud Key Firm v0.6.1 Host Remote Command Execution attempt (1:2024548)
ET TROJAN DNS Query for known ShadowPad CnC 1 (1:2024588)
ET TROJAN DNS Query for known ShadowPad CnC 10 (1:2024597)
ET TROJAN DNS Query for known ShadowPad CnC 11 (1:2024598)
ET TROJAN DNS Query for known ShadowPad CnC 2 (1:2024589)
ET TROJAN DNS Query for known ShadowPad CnC 3 (1:2024590)
ET TROJAN DNS Query for known ShadowPad CnC 4 (1:2024591)
ET TROJAN DNS Query for known ShadowPad CnC 5 (1:2024592)
ET TROJAN DNS Query for known ShadowPad CnC 6 (1:2024593)
ET TROJAN DNS Query for known ShadowPad CnC 7 (1:2024594)
ET TROJAN DNS Query for known ShadowPad CnC 8 (1:2024595)
ET TROJAN DNS Query for known ShadowPad CnC 9 (1:2024596)
ET TROJAN MSIL/CoalaBot CnC Activity (1:2024531)
ET TROJAN OSX.Pwnet.A Certificate Observed (1:2024613)
ET TROJAN Observed DNS Query to Gryphon CnC Domain / GlobeImposter Payment Domain (1:2024543)
ET TROJAN Spora Ransomware DNS Query (1:2024603)
ET TROJAN Win32/Datper CnC Activity (1:2024601)
ET TROJAN [PTsecurity] Gozi/Ursnif Payload v12 (1:2024533)
FILE-EXECUTABLE SandboxEscaper WER download attempt (1:43632)
FILE-EXECUTABLE SandboxEscaper WER download attempt (1:43633)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43638)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43639)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43640)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43641)
FILE-OFFICE Microsoft Office Excel invalid FRTWrapper record buffer overflow attempt (1:43698)
FILE-OFFICE Microsoft Office Excel invalid FRTWrapper record buffer overflow attempt (1:43699)
FILE-OFFICE Microsoft Office RTF parsing remote code execution attempt (1:43678)
FILE-OFFICE Microsoft Office RTF parsing remote code execution attempt (1:43679)
FILE-OFFICE Microsoft Office Word SmartTag record code execution attempt (1:43674)
FILE-OFFICE Microsoft Office Word SmartTag record code execution attempt (1:43675)
FILE-OTHER Aktiv Player wma file buffer overflow attempt (1:43540)
FILE-OTHER Aktiv Player wma file buffer overflow attempt (1:43541)
FILE-OTHER IBM Informix Client SDK NFX file HostList processing stack buffer overflow attempt (1:43623)
FILE-OTHER IBM Informix Client SDK NFX file InformixServerList processing stack buffer overflow attempt (1:43624)
FILE-OTHER ImageMagick SGI ZSIZE header information overflow attempt (1:43608)
FILE-OTHER ImageMagick SGI ZSIZE header information overflow attempt (1:43609)
FILE-OTHER Node.js JS-YAML js function tag code execution attempt (1:43669)
FILE-OTHER Node.js JS-YAML js function tag code execution attempt (1:43670)
FILE-OTHER Oracle Outside-In JPEG2000 QCD segment processing heap buffer overflow attempt (1:43560)
FILE-OTHER Orbital Viewer .orb stack buffer overflow attempt (1:43615)
FILE-OTHER Schneider Electric ClearSCADA malicious OPF file (1:43603)
FILE-OTHER Schneider Electric ClearSCADA malicious OPF file (1:43604)
FILE-OTHER Schneider Electric MaxStream Configuration X-CTU code execution attempt (1:43626)
FILE-OTHER Schneider Electric MaxStream Configuration X-CTU code execution attempt (1:43627)
FILE-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43600)
FILE-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43601)
FILE-OTHER Xion Media Player AIFF denial of service attempt (1:43682)
FILE-OTHER Xion Media Player AIFF denial of service attempt (1:43683)
FILE-OTHER multiple vulnerabilities malformed .m3u file buffer overflow attempt (1:43543)
FILE-OTHER multiple vulnerabilities malformed .wav file buffer overflow attempt (1:43582)
FILE-PDF FreeType PostScript Type1 font parsing memory corruption attempt (1:43676)
FILE-PDF FreeType PostScript Type1 font parsing memory corruption attempt (1:43677)
INDICATOR-COMPROMISE Juniper vSRX Application Firewall IPv6 REJECT buffer overflow attempt (1:43546)
INDICATOR-COMPROMISE Suspicious .top dns query (1:43687)
INDICATOR-COMPROMISE possible Samsung DVR authentication bypass attempt (1:43576)
INDICATOR-OBFUSCATION obfuscated vbscript detected (1:43707)
INDICATOR-OBFUSCATION obfuscated vbscript detected (1:43708)
MALWARE-CNC Andr.Trojan.Femas variant outbound connection (1:43981)
MALWARE-CNC Andr.Trojan.Femas variant outbound connection (1:43982)
MALWARE-CNC Android.Trojan.DroidKungFu outbound connection (1:43578)
MALWARE-CNC Win.Trojan.BlackEnergy outbound communication (1:43597)
MALWARE-CNC Win.Trojan.Fareit variant outbound connection (1:43972)
MALWARE-CNC Win32.Trojan.NeutrinoPOS connection attempt (1:43575)
MALWARE-OTHER Win.Trojan.Nemucod variant file download (1:43684)
MALWARE-OTHER Win.Trojan.Nemucod variant outbound connection (1:43685)
MALWARE-OTHER Win.Trojan.NemucodAES variant outbound connection (1:43686)
OS-LINUX Linux kernel SCTP invalid chunk length denial of service attempt (1:43692)
POLICY-OTHER Cisco DDR2200 ASDL gateway file download detected (1:44004)
SERVER-APACHE httpd ap_find_token buffer overread attempt (1:43587)
SERVER-APACHE httpd mod_mime content-type buffer overflow attempt (1:43547)
SERVER-ORACLE Oracle Reports Server information disclosure attempt (1:43660)
SERVER-ORACLE Oracle Reports Servlet information disclosure attempt (1:43661)
SERVER-ORACLE Oracle Reports Servlet information disclosure attempt (1:43662)
SERVER-OTHER Aerospike Database Server si_prop stack buffer overflow attempt (1:43561)
SERVER-OTHER CCProxy telnet ping buffer overflow attempt (1:43542)
SERVER-OTHER Cisco IOS DHCP denial of service attempt (1:43573)
SERVER-OTHER HPE LoadRunner buffer overflow exploitation attempt (1:43705)
SERVER-OTHER LAN Messenger initiation request buffer overflow attempt (1:43566)
SERVER-OTHER Monkey HTTPD null request denial of service attempt (1:43700)
SERVER-OTHER Oracle Database Server authentication bypass attempt (1:43581)
SERVER-OTHER Oracle Demantra information disclosure attempt (1:43596)
SERVER-OTHER Piwigo LocalFiles editor cross-site request forgery attempt (1:43610)
SERVER-OTHER Piwigo LocalFiles editor cross-site request forgery attempt (1:43611)
SERVER-OTHER Real Networks Helix Server RTSP denial of service attempt (1:43620)
SERVER-OTHER Real Networks Helix Server RTSP denial of service attempt (1:43621)
SERVER-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43602)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43534)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43535)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43536)
SERVER-WEBAPP AlienVault Unified Security Manager authentication bypass attempt (1:43549)
SERVER-WEBAPP Axis M3004 remote code execution attempt (1:43625)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43588)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43589)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43590)
SERVER-WEBAPP Brocade Network Advisor remote code execution attempt (1:43548)
SERVER-WEBAPP CA ArcServe information disclosure attempt (1:43544)
SERVER-WEBAPP CA eHealth command injection attempt (1:43583)
SERVER-WEBAPP CA eHealth command injection attempt (1:43584)
SERVER-WEBAPP CA eHealth command injection attempt (1:43585)
SERVER-WEBAPP CA eHealth command injection attempt (1:43586)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44005)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44006)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44007)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44008)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43616)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43617)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43618)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43619)
SERVER-WEBAPP HPE System Management Homepage buffer overflow attempt (1:43545)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43591)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43592)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43593)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43594)
SERVER-WEBAPP Koha directory traversal attempt (1:43539)
SERVER-WEBAPP Mantis Bug Tracker password reset attempt (1:43693)
SERVER-WEBAPP Mantis Bug Tracker password reset attempt (1:43694)
SERVER-WEBAPP Netgear Prosafe filesystem denial of service attempt (1:43595)
SERVER-WEBAPP Oracle Application Framework diagnostic information disclosure attempt (1:43567)
SERVER-WEBAPP Oracle Application Framework diagnostic information disclosure attempt (1:43568)
SERVER-WEBAPP Oracle BPEL Process Manager directory traversal attempt (1:43577)
SERVER-WEBAPP PHP core unserialize use after free attempt (1:43668)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43653)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43654)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43655)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43552)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43553)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43554)
SERVER-WEBAPP SAP Internet Transaction Server cross site scripting attempt (1:43637)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43645)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43646)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43647)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43688)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43689)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43690)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43695)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43696)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43697)
SERVER-WEBAPP Ubiquiti Networks UniFi Cloud Key Firm v0.6.1 Host Remote Command Execution attempt SERVER-WEBAPP VirtualSystem VS-News-System remote file include attempt (1:43667)
SERVER-WEBAPP Wing FTP Server command injection attempt (1:43574)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43569)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43570)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43571)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43572)
SERVER-WEBAPP Zenoss call home remote code execution attempt (1:43634)
SERVER-WEBAPP phpSecurePages secure.php remote file include attempt (1:43680)
SERVER-WEBAPP phpSecurePages secure.php remote file include attempt (1:43681)
SQL Oracle MySQL Pluggable Auth denial of service attempt (1:43671)
Deleted Rules
BLACKLIST DNS request for known malware domain cinebergen.nl - Win.Trojan.Larosden (1:32032)
BLACKLIST DNS request for known malware domain somee.com - Win.Trojan.Soaphrish (1:32200)
ET TOR Known Tor Exit Node TCP Traffic group 73 (1:2520144)
ET TOR Known Tor Exit Node UDP Traffic group 73 (1:2520145)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 661 (1:2523320)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 662 (1:2523322)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 663 (1:2523324)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 664 (1:2523326)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 665 (1:2523328)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 666 (1:2523330)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 667 (1:2523332)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 668 (1:2523334)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 669 (1:2523336)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 670 (1:2523338)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 671 (1:2523340)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 672 (1:2523342)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 673 (1:2523344)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 674 (1:2523346)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 675 (1:2523348)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 676 (1:2523350)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 677 (1:2523352)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 661 (1:2523321)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 662 (1:2523323)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 663 (1:2523325)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 664 (1:2523327)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 665 (1:2523329)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 666 (1:2523331)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 667 (1:2523333)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 668 (1:2523335)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 669 (1:2523337)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 670 (1:2523339)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 671 (1:2523341)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 672 (1:2523343)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 673 (1:2523345)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 674 (1:2523347)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 675 (1:2523349)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 676 (1:2523351)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 677 (1:2523353)
SERVER-WEBAPP Invalid HTTP Version String (1:43762)
Rule Totals
New:-------257
Deleted:---39
Enabled:---29379
Dropped:---0
Disabled:--26706
Total:-----56085
IP Blacklist Stats
Total IPs:-----8908
Gerando uma estatística manual das categorias adicionadas temos:
Adicionadas:
63 ET CURRENT_EVENTS
63 SERVER-WEBAPP
20 FILE-OTHER
17 ET TROJAN
16 BROWSER-IE
13 SERVER-OTHER
11 BROWSER-PLUGINS
10 FILE-OFFICE
8 BROWSER-FIREFOX
6 MALWARE-CNC
6 ET CNC
3 SERVER-ORACLE
3 MALWARE-OTHER
3 INDICATOR-COMPROMISE
2 SERVER-APACHE
2 INDICATOR-OBFUSCATION
2 FILE-PDF
2 FILE-EXECUTABLE
2 ET DOS
1 SQL
1 POLICY-OTHER
1 OS-LINUX
1 ET EXPLOIT
1 APP-DETECT HTTPTunnel
O arquivo basicamente vem demonstrando todas as regras adicionadas, o que é bem interessante quando monitoramento para ver tendências como baseado nas categorias mais atualizadas ou deletadas. Além disso é de suma importância sempre deixar o IDS atualizado, pois como podem ver regras são deletadas, por não fazerem mais sentido ou até por detecção ruim, que certamente floodará seu SOC com falsos positivos.
Lembrando que também é feito a update da lista de IP's utilizados pelo preprocessador de IP Reputation que deve ser configurado em seu snort.conf para ter o benefício dessa listagem, que até mais que as regras são bem dinâmicas.
Como citado anteriormente, esperamos nas próximas edições do SRW termos mais conteúdos derivado de análises e honeypots.
Happy Detection!
Threat Hunter Brasil Team
Explicando o que é o PulledPork, em resumo é uma ferramenta de atualização e gerenciamento de regras para Suricata / Snort IDS. Seu código pode ser analisado e estudado em https://github.com/shirkdog/pulledpork.
New Rules
APP-DETECT HTTPTunnel proxy outbound connection detected (1:43565)
BROWSER-FIREFOX Mozilla Firefox Javascript contentWindow in an iframe exploit attempt (1:43706)
BROWSER-FIREFOX Mozilla Firefox design mode deleted style memory corruption attempt (1:43643)
BROWSER-FIREFOX Mozilla Firefox display moz-deck style memory corruption attempt (1:43644)
BROWSER-FIREFOX Mozilla Firefox large window null pointer dereference attempt (1:43651)
BROWSER-FIREFOX Mozilla Firefox large window null pointer dereference attempt (1:43652)
BROWSER-FIREFOX Mozilla Firefox multiple vulnerabilities memory corruption attempt (1:43642)
BROWSER-FIREFOX Mozilla products obfuscated cross site scripting attempt (1:43672)
BROWSER-FIREFOX Mozilla products obfuscated cross site scripting attempt (1:43673)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43656)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43657)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43658)
BROWSER-IE Microsoft Edge JavaScript ReverseHelper buffer overrun attempt (1:43659)
BROWSER-IE Microsoft Internet Explorer 11 CMarkup GetMarkupTitle use-after-free attempt (1:43664)
BROWSER-IE Microsoft Internet Explorer 11 CMarkup GetMarkupTitle use-after-free attempt (1:43665)
BROWSER-IE Microsoft Internet Explorer CDocument use after free attempt (1:43648)
BROWSER-IE Microsoft Internet Explorer EUC-JP encoding cross site scripting attempt (1:43635)
BROWSER-IE Microsoft Internet Explorer EUC-JP encoding cross site scripting attempt (1:43636)
BROWSER-IE Microsoft Internet Explorer GDI VML gradient size heap overflow attempt (1:43622)
BROWSER-IE Microsoft Internet Explorer object type confusion remote code execution attempt (1:43598)
BROWSER-IE Microsoft Internet Explorer object type confusion remote code execution attempt (1:43599)
BROWSER-IE Microsoft Internet Explorer span tag memory corruption attempt (1:43550)
BROWSER-IE Microsoft Internet Explorer span tag memory corruption attempt (1:43551)
BROWSER-IE Microsoft Internet Explorer type confusion attempt (1:43579)
BROWSER-IE Microsoft Internet Explorer type confusion attempt (1:43580)
BROWSER-PLUGINS HP Photo Creative ActiveX clsid access attempt (1:43607)
BROWSER-PLUGINS IBM SPSS Statistics ActiveX clsid access attempt (1:43537)
BROWSER-PLUGINS IBM SPSS Statistics ActiveX clsid access attempt (1:43538)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43701)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43702)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43703)
BROWSER-PLUGINS McAfee FreeScan information disclosure ActiveX clsid access attempt (1:43704)
BROWSER-PLUGINS Microsoft Access Snapshot Viewer ActiveX function call access attempt (1:43605)
BROWSER-PLUGINS Microsoft Access Snapshot Viewer ActiveX function call access attempt (1:43606)
BROWSER-PLUGINS Ultra Crypto Component ActiveX clsid access attempt (1:43649)
BROWSER-PLUGINS Ultra Crypto Component ActiveX clsid access attempt (1:43650)
ET CNC Ransomware Tracker Reported CnC Server TCP group 159 (1:2404716)
ET CNC Ransomware Tracker Reported CnC Server UDP group 159 (1:2404717)
ET CNC Shadowserver Reported CnC Server Port 33333 Group 1 (1:2405067)
ET CNC Shadowserver Reported CnC Server Port 40669 Group 1 (1:2405068)
ET CNC Shadowserver Reported CnC Server TCP group 49 (1:2404096)
ET CNC Shadowserver Reported CnC Server UDP group 49 (1:2404097)
ET CURRENT_EVENTS Disdain EK Flash Exploit M1 Aug 23 2017 (1:2024609)
ET CURRENT_EVENTS Disdain EK Flash Exploit M2 Aug 23 2017 (1:2024610)
ET CURRENT_EVENTS Disdain EK Flash Exploit M3 Aug 23 2017 (1:2024611)
ET CURRENT_EVENTS Disdain EK Landing Aug 23 2017 (1:2024612)
ET CURRENT_EVENTS Disdain EK Payload Aug 23 2017 (1:2024608)
ET CURRENT_EVENTS Disdain EK URI Struct Aug 23 2017 M1 (1:2024606)
ET CURRENT_EVENTS Disdain EK URI Struct Aug 23 2017 M2 (1:2024607)
ET CURRENT_EVENTS Hancitor/Tordal Document Inbound (1:2024605)
ET CURRENT_EVENTS Hancitor/Tordal Document Request (1:2024604)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP AX (1:2024553)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP AX M2 (1:2024602)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M1 (1:2024550)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M2 (1:2024551)
ET CURRENT_EVENTS Likely Malicious Windows SCT Download MSXMLHTTP M3 (1:2024552)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt (1:2024537)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B641 (1:2024534)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B642 (1:2024535)
ET CURRENT_EVENTS Possible AMSI Powershell Bypass Attempt B643 (1:2024536)
ET CURRENT_EVENTS Possible Maldoc Downloader Aug 18 2017 (1:2024600)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Aug 19 2016 (1:2024560)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 07 2016 (1:2024568)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 13 2016 (1:2024569)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 20 2016 (1:2024570)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Dec 27 2016 (1:2024571)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024554)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024555)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Feb 26 (1:2024556)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 03 2017 (1:2024572)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 12 2017 (1:2024573)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 17 2017 (1:2024574)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jan 17 2017 (1:2024575)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 06 2017 (1:2024580)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 10 2017 (1:2024581)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 11 2017 (1:2024582)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jul 13 (1:2024558)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jun 08 2017 (1:2024579)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Jun 8 (1:2024557)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 24 2017 (1:2024576)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 25 2017 (1:2024577)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) May 31 2017 (1:2024578)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 15 2016 (1:2024565)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 16 2016 (1:2024566)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Nov 22 2016 (1:2024567)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 13 (1:2024562)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 25 (1:2024563)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Oct 26 (1:2024564)
ET CURRENT_EVENTS Possible Successful Generic Phish (set) Sept 2 (1:2024561)
ET CURRENT_EVENTS Possible Successful Phish - Verify Email Error Message M1 Aug 14 2017 (1:2024541)
ET CURRENT_EVENTS Possible Successful Phish - Verify Email Error Message M2 Aug 14 2017 (1:2024542)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B641 (1:2024538)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B642 (1:2024539)
ET CURRENT_EVENTS Possible Veil Powershell Encoder B643 (1:2024540)
ET CURRENT_EVENTS Possible YapiKredi Bank (TR) Phish - Landing Page - Title over non SSL (1:2024583)
ET CURRENT_EVENTS Successful Adobe Online Phish Aug 16 2016 (1:2024559)
ET CURRENT_EVENTS Successful Interac Phish Aug 18 2017 (1:2024599)
ET CURRENT_EVENTS Successful Mail.ru Phish Aug 10 2017 (1:2024532)
ET CURRENT_EVENTS Successful Paypal Phish M1 Aug 14 2017 (1:2024544)
ET CURRENT_EVENTS Successful Paypal Phish M2 Aug 14 2017 (1:2024545)
ET CURRENT_EVENTS Successful Paypal Phish M3 Aug 14 2017 (1:2024546)
ET CURRENT_EVENTS Successful RBC Royal Bank Phish M1 Aug 17 2017 (1:2024586)
ET CURRENT_EVENTS Successful RBC Royal Bank Phish M2 Aug 17 2017 (1:2024587)
ET CURRENT_EVENTS Successful Square Phish Nov 16 2015 (1:2024547)
ET CURRENT_EVENTS Windows Scriptlet Invoking Powershell Likely Malicious (1:2024549)
ET DOS CLDAP Amplification Reflection (PoC based) (1:2024584)
ET DOS Potential CLDAP Amplification Reflection (1:2024585)
ET EXPLOIT Ubiquiti Networks UniFi Cloud Key Firm v0.6.1 Host Remote Command Execution attempt (1:2024548)
ET TROJAN DNS Query for known ShadowPad CnC 1 (1:2024588)
ET TROJAN DNS Query for known ShadowPad CnC 10 (1:2024597)
ET TROJAN DNS Query for known ShadowPad CnC 11 (1:2024598)
ET TROJAN DNS Query for known ShadowPad CnC 2 (1:2024589)
ET TROJAN DNS Query for known ShadowPad CnC 3 (1:2024590)
ET TROJAN DNS Query for known ShadowPad CnC 4 (1:2024591)
ET TROJAN DNS Query for known ShadowPad CnC 5 (1:2024592)
ET TROJAN DNS Query for known ShadowPad CnC 6 (1:2024593)
ET TROJAN DNS Query for known ShadowPad CnC 7 (1:2024594)
ET TROJAN DNS Query for known ShadowPad CnC 8 (1:2024595)
ET TROJAN DNS Query for known ShadowPad CnC 9 (1:2024596)
ET TROJAN MSIL/CoalaBot CnC Activity (1:2024531)
ET TROJAN OSX.Pwnet.A Certificate Observed (1:2024613)
ET TROJAN Observed DNS Query to Gryphon CnC Domain / GlobeImposter Payment Domain (1:2024543)
ET TROJAN Spora Ransomware DNS Query (1:2024603)
ET TROJAN Win32/Datper CnC Activity (1:2024601)
ET TROJAN [PTsecurity] Gozi/Ursnif Payload v12 (1:2024533)
FILE-EXECUTABLE SandboxEscaper WER download attempt (1:43632)
FILE-EXECUTABLE SandboxEscaper WER download attempt (1:43633)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43638)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43639)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43640)
FILE-OFFICE Microsoft Excel null pointer dereference attempt (1:43641)
FILE-OFFICE Microsoft Office Excel invalid FRTWrapper record buffer overflow attempt (1:43698)
FILE-OFFICE Microsoft Office Excel invalid FRTWrapper record buffer overflow attempt (1:43699)
FILE-OFFICE Microsoft Office RTF parsing remote code execution attempt (1:43678)
FILE-OFFICE Microsoft Office RTF parsing remote code execution attempt (1:43679)
FILE-OFFICE Microsoft Office Word SmartTag record code execution attempt (1:43674)
FILE-OFFICE Microsoft Office Word SmartTag record code execution attempt (1:43675)
FILE-OTHER Aktiv Player wma file buffer overflow attempt (1:43540)
FILE-OTHER Aktiv Player wma file buffer overflow attempt (1:43541)
FILE-OTHER IBM Informix Client SDK NFX file HostList processing stack buffer overflow attempt (1:43623)
FILE-OTHER IBM Informix Client SDK NFX file InformixServerList processing stack buffer overflow attempt (1:43624)
FILE-OTHER ImageMagick SGI ZSIZE header information overflow attempt (1:43608)
FILE-OTHER ImageMagick SGI ZSIZE header information overflow attempt (1:43609)
FILE-OTHER Node.js JS-YAML js function tag code execution attempt (1:43669)
FILE-OTHER Node.js JS-YAML js function tag code execution attempt (1:43670)
FILE-OTHER Oracle Outside-In JPEG2000 QCD segment processing heap buffer overflow attempt (1:43560)
FILE-OTHER Orbital Viewer .orb stack buffer overflow attempt (1:43615)
FILE-OTHER Schneider Electric ClearSCADA malicious OPF file (1:43603)
FILE-OTHER Schneider Electric ClearSCADA malicious OPF file (1:43604)
FILE-OTHER Schneider Electric MaxStream Configuration X-CTU code execution attempt (1:43626)
FILE-OTHER Schneider Electric MaxStream Configuration X-CTU code execution attempt (1:43627)
FILE-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43600)
FILE-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43601)
FILE-OTHER Xion Media Player AIFF denial of service attempt (1:43682)
FILE-OTHER Xion Media Player AIFF denial of service attempt (1:43683)
FILE-OTHER multiple vulnerabilities malformed .m3u file buffer overflow attempt (1:43543)
FILE-OTHER multiple vulnerabilities malformed .wav file buffer overflow attempt (1:43582)
FILE-PDF FreeType PostScript Type1 font parsing memory corruption attempt (1:43676)
FILE-PDF FreeType PostScript Type1 font parsing memory corruption attempt (1:43677)
INDICATOR-COMPROMISE Juniper vSRX Application Firewall IPv6 REJECT buffer overflow attempt (1:43546)
INDICATOR-COMPROMISE Suspicious .top dns query (1:43687)
INDICATOR-COMPROMISE possible Samsung DVR authentication bypass attempt (1:43576)
INDICATOR-OBFUSCATION obfuscated vbscript detected (1:43707)
INDICATOR-OBFUSCATION obfuscated vbscript detected (1:43708)
MALWARE-CNC Andr.Trojan.Femas variant outbound connection (1:43981)
MALWARE-CNC Andr.Trojan.Femas variant outbound connection (1:43982)
MALWARE-CNC Android.Trojan.DroidKungFu outbound connection (1:43578)
MALWARE-CNC Win.Trojan.BlackEnergy outbound communication (1:43597)
MALWARE-CNC Win.Trojan.Fareit variant outbound connection (1:43972)
MALWARE-CNC Win32.Trojan.NeutrinoPOS connection attempt (1:43575)
MALWARE-OTHER Win.Trojan.Nemucod variant file download (1:43684)
MALWARE-OTHER Win.Trojan.Nemucod variant outbound connection (1:43685)
MALWARE-OTHER Win.Trojan.NemucodAES variant outbound connection (1:43686)
OS-LINUX Linux kernel SCTP invalid chunk length denial of service attempt (1:43692)
POLICY-OTHER Cisco DDR2200 ASDL gateway file download detected (1:44004)
SERVER-APACHE httpd ap_find_token buffer overread attempt (1:43587)
SERVER-APACHE httpd mod_mime content-type buffer overflow attempt (1:43547)
SERVER-ORACLE Oracle Reports Server information disclosure attempt (1:43660)
SERVER-ORACLE Oracle Reports Servlet information disclosure attempt (1:43661)
SERVER-ORACLE Oracle Reports Servlet information disclosure attempt (1:43662)
SERVER-OTHER Aerospike Database Server si_prop stack buffer overflow attempt (1:43561)
SERVER-OTHER CCProxy telnet ping buffer overflow attempt (1:43542)
SERVER-OTHER Cisco IOS DHCP denial of service attempt (1:43573)
SERVER-OTHER HPE LoadRunner buffer overflow exploitation attempt (1:43705)
SERVER-OTHER LAN Messenger initiation request buffer overflow attempt (1:43566)
SERVER-OTHER Monkey HTTPD null request denial of service attempt (1:43700)
SERVER-OTHER Oracle Database Server authentication bypass attempt (1:43581)
SERVER-OTHER Oracle Demantra information disclosure attempt (1:43596)
SERVER-OTHER Piwigo LocalFiles editor cross-site request forgery attempt (1:43610)
SERVER-OTHER Piwigo LocalFiles editor cross-site request forgery attempt (1:43611)
SERVER-OTHER Real Networks Helix Server RTSP denial of service attempt (1:43620)
SERVER-OTHER Real Networks Helix Server RTSP denial of service attempt (1:43621)
SERVER-OTHER Wireshark ENTTEC DMX RLE buffer overflow attempt (1:43602)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43534)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43535)
SERVER-WEBAPP AlienVault OSSIM nfsen.php command injection attempt (1:43536)
SERVER-WEBAPP AlienVault Unified Security Manager authentication bypass attempt (1:43549)
SERVER-WEBAPP Axis M3004 remote code execution attempt (1:43625)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43588)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43589)
SERVER-WEBAPP Brocade Network Advisor directory traversal attempt (1:43590)
SERVER-WEBAPP Brocade Network Advisor remote code execution attempt (1:43548)
SERVER-WEBAPP CA ArcServe information disclosure attempt (1:43544)
SERVER-WEBAPP CA eHealth command injection attempt (1:43583)
SERVER-WEBAPP CA eHealth command injection attempt (1:43584)
SERVER-WEBAPP CA eHealth command injection attempt (1:43585)
SERVER-WEBAPP CA eHealth command injection attempt (1:43586)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44005)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44006)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44007)
SERVER-WEBAPP Cisco DDR2200 ADSL gateway command injection attempt (1:44008)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43616)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43617)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43618)
SERVER-WEBAPP E-Mail Security Virtual Appliance command injection attempt (1:43619)
SERVER-WEBAPP HPE System Management Homepage buffer overflow attempt (1:43545)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43591)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43592)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43593)
SERVER-WEBAPP IBM Tealeaf testconn_host command injection attempt (1:43594)
SERVER-WEBAPP Koha directory traversal attempt (1:43539)
SERVER-WEBAPP Mantis Bug Tracker password reset attempt (1:43693)
SERVER-WEBAPP Mantis Bug Tracker password reset attempt (1:43694)
SERVER-WEBAPP Netgear Prosafe filesystem denial of service attempt (1:43595)
SERVER-WEBAPP Oracle Application Framework diagnostic information disclosure attempt (1:43567)
SERVER-WEBAPP Oracle Application Framework diagnostic information disclosure attempt (1:43568)
SERVER-WEBAPP Oracle BPEL Process Manager directory traversal attempt (1:43577)
SERVER-WEBAPP PHP core unserialize use after free attempt (1:43668)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43653)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43654)
SERVER-WEBAPP Pheap edit.php directory traversal attempt (1:43655)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43552)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43553)
SERVER-WEBAPP ReadyDesk upload remote code execution attempt (1:43554)
SERVER-WEBAPP SAP Internet Transaction Server cross site scripting attempt (1:43637)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43645)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43646)
SERVER-WEBAPP SonicWall Secure Remote Access diagnostics command injection attempt (1:43647)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43688)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43689)
SERVER-WEBAPP SonicWall Secure Remote Access viewcert command injection attempt (1:43690)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43695)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43696)
SERVER-WEBAPP Trend Micro InterScan WSA DeployWizard command injection attempt (1:43697)
SERVER-WEBAPP Ubiquiti Networks UniFi Cloud Key Firm v0.6.1 Host Remote Command Execution attempt SERVER-WEBAPP VirtualSystem VS-News-System remote file include attempt (1:43667)
SERVER-WEBAPP Wing FTP Server command injection attempt (1:43574)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43569)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43570)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43571)
SERVER-WEBAPP Zavio Cam command injection attempt (1:43572)
SERVER-WEBAPP Zenoss call home remote code execution attempt (1:43634)
SERVER-WEBAPP phpSecurePages secure.php remote file include attempt (1:43680)
SERVER-WEBAPP phpSecurePages secure.php remote file include attempt (1:43681)
SQL Oracle MySQL Pluggable Auth denial of service attempt (1:43671)
Deleted Rules
BLACKLIST DNS request for known malware domain cinebergen.nl - Win.Trojan.Larosden (1:32032)
BLACKLIST DNS request for known malware domain somee.com - Win.Trojan.Soaphrish (1:32200)
ET TOR Known Tor Exit Node TCP Traffic group 73 (1:2520144)
ET TOR Known Tor Exit Node UDP Traffic group 73 (1:2520145)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 661 (1:2523320)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 662 (1:2523322)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 663 (1:2523324)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 664 (1:2523326)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 665 (1:2523328)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 666 (1:2523330)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 667 (1:2523332)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 668 (1:2523334)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 669 (1:2523336)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 670 (1:2523338)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 671 (1:2523340)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 672 (1:2523342)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 673 (1:2523344)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 674 (1:2523346)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 675 (1:2523348)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 676 (1:2523350)
ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 677 (1:2523352)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 661 (1:2523321)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 662 (1:2523323)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 663 (1:2523325)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 664 (1:2523327)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 665 (1:2523329)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 666 (1:2523331)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 667 (1:2523333)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 668 (1:2523335)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 669 (1:2523337)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 670 (1:2523339)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 671 (1:2523341)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 672 (1:2523343)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 673 (1:2523345)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 674 (1:2523347)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 675 (1:2523349)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 676 (1:2523351)
ET TOR Known Tor Relay/Router (Not Exit) Node UDP Traffic group 677 (1:2523353)
SERVER-WEBAPP Invalid HTTP Version String (1:43762)
Rule Totals
New:-------257
Deleted:---39
Enabled:---29379
Dropped:---0
Disabled:--26706
Total:-----56085
IP Blacklist Stats
Total IPs:-----8908
Gerando uma estatística manual das categorias adicionadas temos:
Adicionadas:
63 ET CURRENT_EVENTS
63 SERVER-WEBAPP
20 FILE-OTHER
17 ET TROJAN
16 BROWSER-IE
13 SERVER-OTHER
11 BROWSER-PLUGINS
10 FILE-OFFICE
8 BROWSER-FIREFOX
6 MALWARE-CNC
6 ET CNC
3 SERVER-ORACLE
3 MALWARE-OTHER
3 INDICATOR-COMPROMISE
2 SERVER-APACHE
2 INDICATOR-OBFUSCATION
2 FILE-PDF
2 FILE-EXECUTABLE
2 ET DOS
1 SQL
1 POLICY-OTHER
1 OS-LINUX
1 ET EXPLOIT
1 APP-DETECT HTTPTunnel
O arquivo basicamente vem demonstrando todas as regras adicionadas, o que é bem interessante quando monitoramento para ver tendências como baseado nas categorias mais atualizadas ou deletadas. Além disso é de suma importância sempre deixar o IDS atualizado, pois como podem ver regras são deletadas, por não fazerem mais sentido ou até por detecção ruim, que certamente floodará seu SOC com falsos positivos.
Lembrando que também é feito a update da lista de IP's utilizados pelo preprocessador de IP Reputation que deve ser configurado em seu snort.conf para ter o benefício dessa listagem, que até mais que as regras são bem dinâmicas.
Como citado anteriormente, esperamos nas próximas edições do SRW termos mais conteúdos derivado de análises e honeypots.
Happy Detection!
Threat Hunter Brasil Team
Assinar:
Postagens (Atom)