ATT&CK Introduction (retrieved from mitre attack website)
"Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) for Enterprise is an adversary model and framework for describing the actions an adversary may take to compromise and operate within an enterprise network. The model can be used to better characterize and describe post-compromise adversary behavior. It both expands the knowledge of network defenders and assists in prioritizing network defense by detailing the tactics, techniques, and procedures (TTPs) cyber threats use to gain access and execute their objectives while operating inside a network.
ATT&CK for Enterprise incorporates information on cyber adversaries gathered through MITRE research, as well as from other disciplines such as penetration testing and red teaming to establish a collection of knowledge characterizing the activities adversaries use against enterprise networks. While there is significant research on initial exploitation and use of perimeter defenses, there is a gap in central knowledge of adversary process after initial access has been gained. ATT&CK for Enterprise focuses on TTPs adversaries use to make decisions, expand access, and execute their objectives. It aims to describe an adversary's steps at a high enough level to be applied widely across platforms, but still maintain enough details to be technically useful.
The 11 tactic categories within ATT&CK for Enterprise were derived from the later stages (exploit, control, maintain, and execute) of a seven-stage Cyber Attack Lifecycle[1] (first articulated by Lockheed Martin as the Cyber Kill Chain®[2]). This provides a deeper level of granularity in describing what can occur during an intrusion.
Each category contains a list of techniques that an adversary could use to perform that tactic. Techniques are broken down to provide a technical description, indicators, useful defensive sensor data, detection analytics, and potential mitigations. Applying intrusion data to the model then helps focus defense on the commonly used techniques across groups of activity and helps identify gaps in security. Defenders and decision makers can use the information in ATT&CK for Enterprise for various purposes, not just as a checklist of specific adversarial techniques.
ATT&CK for Enterprise incorporates details from multiple operating system platforms commonly found within enterprise networks, including Microsoft Windows, macOS, and Linux. The framework and higher level categories may also be applied to other platforms and environments. To view the contents of ATT&CK for Enterprise, use the left navigation pane, which breaks out techniques by tactic category or view All Techniques."
Based on ATT&CK we can take a snapshot of our company security state on each tactic and technique, knowing where we have better detection and where we should invest more efforts. So in our mind and talking about this during a ATT&CK training we were teaching, the question was how to create a visualization for this and decide quickly how to prioritize an IDS alert, or a vulnerability found or new technology we need to deploy to cover gaps ? The answer that we found was using Navigator Scoring with Elastic Stack.
ATT&CK for Enterprise incorporates information on cyber adversaries gathered through MITRE research, as well as from other disciplines such as penetration testing and red teaming to establish a collection of knowledge characterizing the activities adversaries use against enterprise networks. While there is significant research on initial exploitation and use of perimeter defenses, there is a gap in central knowledge of adversary process after initial access has been gained. ATT&CK for Enterprise focuses on TTPs adversaries use to make decisions, expand access, and execute their objectives. It aims to describe an adversary's steps at a high enough level to be applied widely across platforms, but still maintain enough details to be technically useful.
The 11 tactic categories within ATT&CK for Enterprise were derived from the later stages (exploit, control, maintain, and execute) of a seven-stage Cyber Attack Lifecycle[1] (first articulated by Lockheed Martin as the Cyber Kill Chain®[2]). This provides a deeper level of granularity in describing what can occur during an intrusion.
Each category contains a list of techniques that an adversary could use to perform that tactic. Techniques are broken down to provide a technical description, indicators, useful defensive sensor data, detection analytics, and potential mitigations. Applying intrusion data to the model then helps focus defense on the commonly used techniques across groups of activity and helps identify gaps in security. Defenders and decision makers can use the information in ATT&CK for Enterprise for various purposes, not just as a checklist of specific adversarial techniques.
ATT&CK for Enterprise incorporates details from multiple operating system platforms commonly found within enterprise networks, including Microsoft Windows, macOS, and Linux. The framework and higher level categories may also be applied to other platforms and environments. To view the contents of ATT&CK for Enterprise, use the left navigation pane, which breaks out techniques by tactic category or view All Techniques."
Based on ATT&CK we can take a snapshot of our company security state on each tactic and technique, knowing where we have better detection and where we should invest more efforts. So in our mind and talking about this during a ATT&CK training we were teaching, the question was how to create a visualization for this and decide quickly how to prioritize an IDS alert, or a vulnerability found or new technology we need to deploy to cover gaps ? The answer that we found was using Navigator Scoring with Elastic Stack.
So how we could do that with them?
Basically Mitre Navigator you can fill techniques with some Score based on tools you have or initially just based on "feelings". After you filled all the techniques you will have something like this:
We really suggest you split into minor areas, network segmentation, department this but in a very first step have a general one is a good start.
So having this read you have how to add Layer Name and Description (In our sample we configure Layer as "Company" and Description as "Network Segment")
After filling your matrix, you can download it as a JSON file. The only problem with JSON I found it was that logstash JSON filter can't parse it directly you I just remove newlines with some basic bash.
Regular JSON download
File ready, time to parse and send it to Elasticsearch. We just created a basic config to create this PoC that we have ideas to enrich with more information in a second part.
Config:
input {stdin {}}
filter {
json { source => message }
split {
field => "techniques"
}
mutate { remove_field => [ "gradient", "filters", "hideDisabled", "tacticRowBackground", "legendItems", "sorting","showTacticRowBackground", "viewMode", "selectTechniquesAcrossTactics","version" , "@version" , "[techniques][color]", "[techniques][enabled]", "message"] }
}
output {elasticsearch { index => navigator }}
Debug Output:
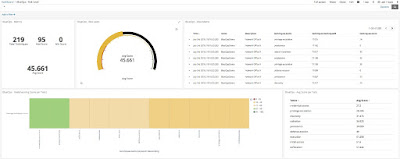
With data ingested in our Elasticsearch we created some views:
To download Kibana stuff https://github.com/spookerlabs/kibana_attack
Some ideas we have in mind for the future:
- Create a database about defense tools mapped with ATT&CK and correlate your status and needs
- Tool to quickly correlate a Pentest/VA report and prioritize vulnerability affects more your network
- Compare you security risk with groups or something you read and map.
- Integrate / Compatibility with HELK project
- Enrich information using translate at logstash
- Auto update scoring using Red Team automation / tests
- Add ATT&CK Pre
If you have something in mind let us know. Hope it helps!
Happy Detection!
Blue Team Operations
- Enrich information using translate at logstash
- Auto update scoring using Red Team automation / tests
- Add ATT&CK Pre
If you have something in mind let us know. Hope it helps!
Happy Detection!
Blue Team Operations






Nenhum comentário:
Postar um comentário